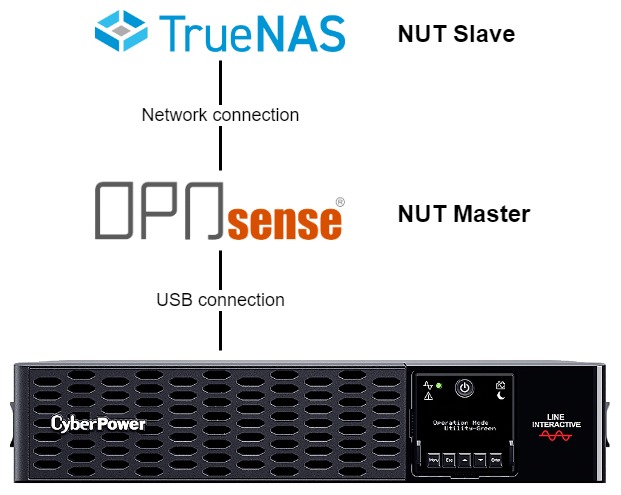
For storage in my homelab, I use TrueNAS. Additionally, I run a couple of apps on top of it as jails. For over a year, I’ve been using an uninterruptible power supply (UPS) to protect my TrueNAS from possible data loss in case of a power failure. What I’ve been missing throughout that time are the monitoring and management tools to shut down everything gracefully when the battery of the UPS runs low. In the event of a power outage lasting longer than 30 minutes, the battery would run out of juice. Everything attached to the UPS would be powered off immediately, and data loss might occur. Luckily I live in an area where power outages rarely happen. I also have backups I could restore if my TrueNAS data gets corrupted. Still, doing this right and configuring Network UPS Tools (NUT) to orchestrate shutdowns has been on my to-do list for way too long. It’s time to tackle the issue!
Self-Host
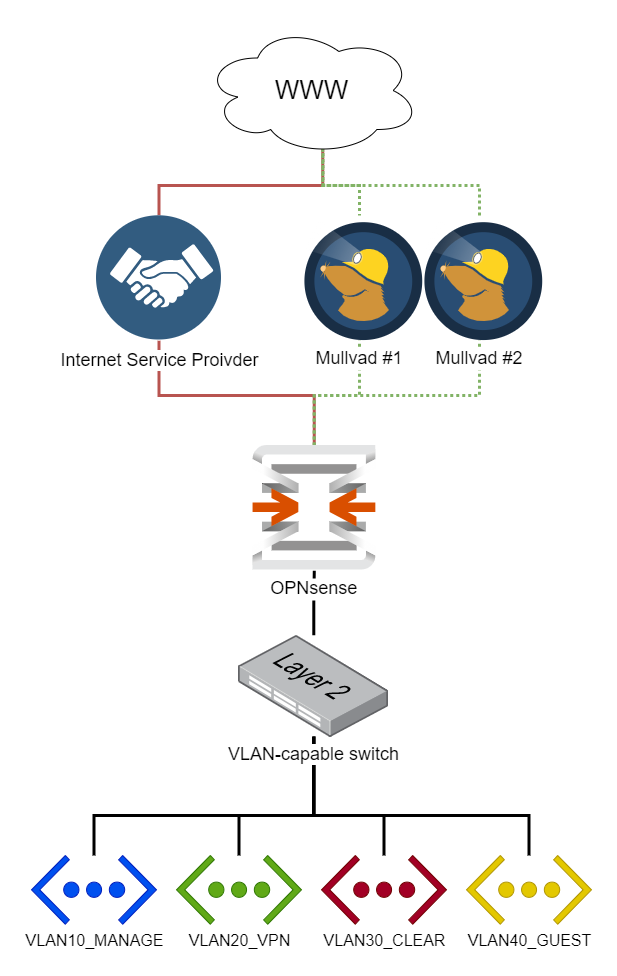
This beginner-friendly, step-by-step guide walks you through the initial configuration of your OPNsense firewall. The title of this guide is an homage to the pfSense baseline guide with VPN, Guest, and VLAN support that some of you guys might know, and this is an OPNsense migration of it. I found that guide two years ago and immediately fell in love with the network setup. After researching for weeks, I decided to use OPNsense instead of pfSense. I bit the bullet and bought the Deciso DEC630 appliance. Albeit expensive and possibly overkill for my needs, I’m happy to support the open-source mission of Deciso, the maintainers of OPNsense. The only thing I regret about the purchase is that I now can’t afford the sexier-looking successor model, the DEC690.
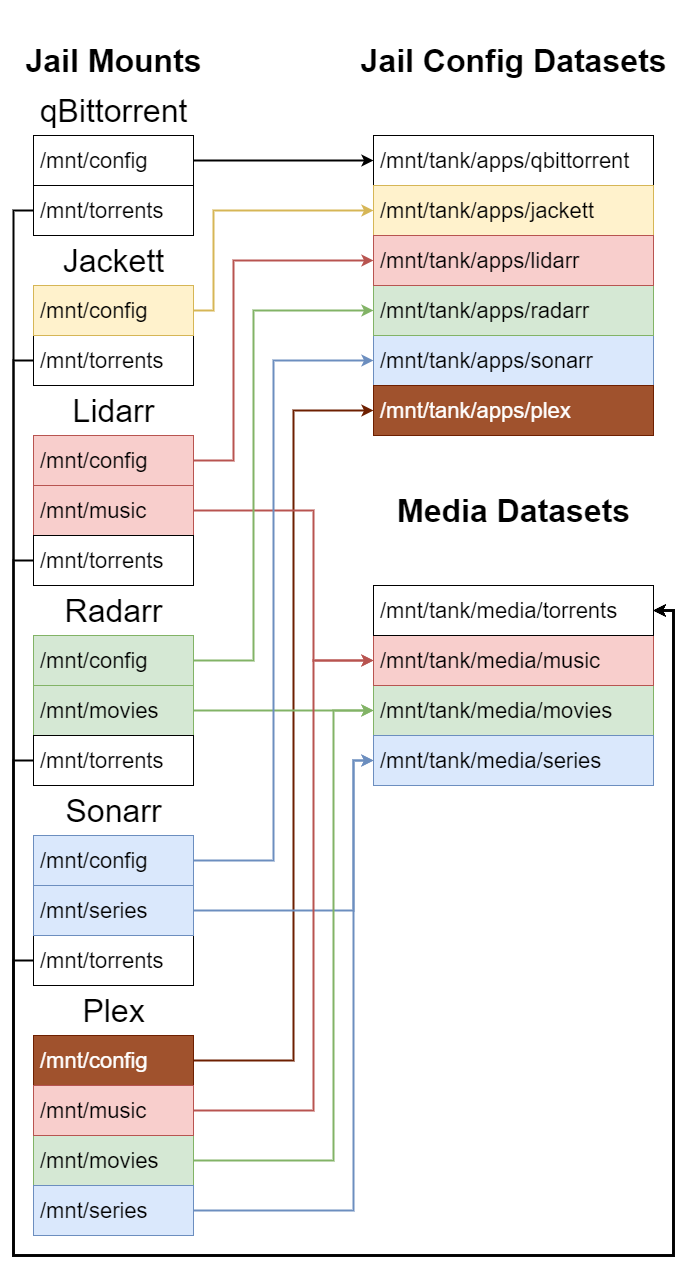
This post documents the steps required to install qBittorrent, Jackett, Lidarr, Radarr, Sonarr, and Plex in TrueNAS jails version 12.0-U6.
To manage Ubiquiti UniFi devices, a UniFi controller is required. Over a year ago, I initially installed the controller software inside a Ubuntu VirtualBox VM. Now that version 6 of the UniFi controller software is released, it’s time to upgrade. I decided to reinstall the controller inside a TrueNAS jail instead of a VirtualBox VM. When searching the interwebs, I only found lots of outdated instructions. It turns out that it’s very straightforward, so here are my quick notes on how to do it.
Did you ever think about running a Matrix homeserver? In this post, we will set one up on the Azure Kubernetes Service (AKS). We will use the reference homeserver implementation, which is Synapse from the folks at matrix.org. This post focuses on the Kubernetes stuff, keeping Synapse configuration to a minimum. Things like federation, delegation and PostgreSQL are out of scope, because plenty of excellent guides and the official documentation exist covering that. The icing on the cake will be the Synapse Admin UI deployment with secure access to the administration endpoints to make management of our homeserver easier.
Building upon our previous work, we will deploy Remark42 on Kubernetes with Terraform and integrate it with your existing Hugo website. Make sure to check out my previous posts about creating a Hugo Website and deploying an Azure Kubernetes Service cluster if you haven’t already.
In this post, we will deploy a simple Azure Kubernetes Service (AKS) cluster from scratch. To expose our web services securely, we will install Traefik 2 and configure cert-manager to manage Let’s Encrypt certificates. The best part about it: we will do everything with Terraform.